ตราปั๊มหรือตราประทับ อุปกรณ์ชิ้นนี้ได้รับความนิยมอย่างมาก ใช้กับเอกสาร การทำธุรกรรมต่างๆ นิยมใช้ในบริษัท องค์กร ปัจจุบันตราปั๊มถูกนำมาใช้พิมพ์โลโก้สินค้า สร้างสีสันได้หลากหลาย เมื่อพูดถึงสีของตราปั๊ม สีที่ได้รับความนิยม มีเพียงไม่กี่สี ได้แก่ หมึกสีแดง หมึกสีดำ หมึกสีน้ำเงิน แล้วทุกคนรู้ไหมว่า สีแต่ละสี มีความสำคัญอย่างไร นำไปใช้ประทับตราเอกสารแบบไหน ทั้งหมดนี้เรามีคำตอบ ...
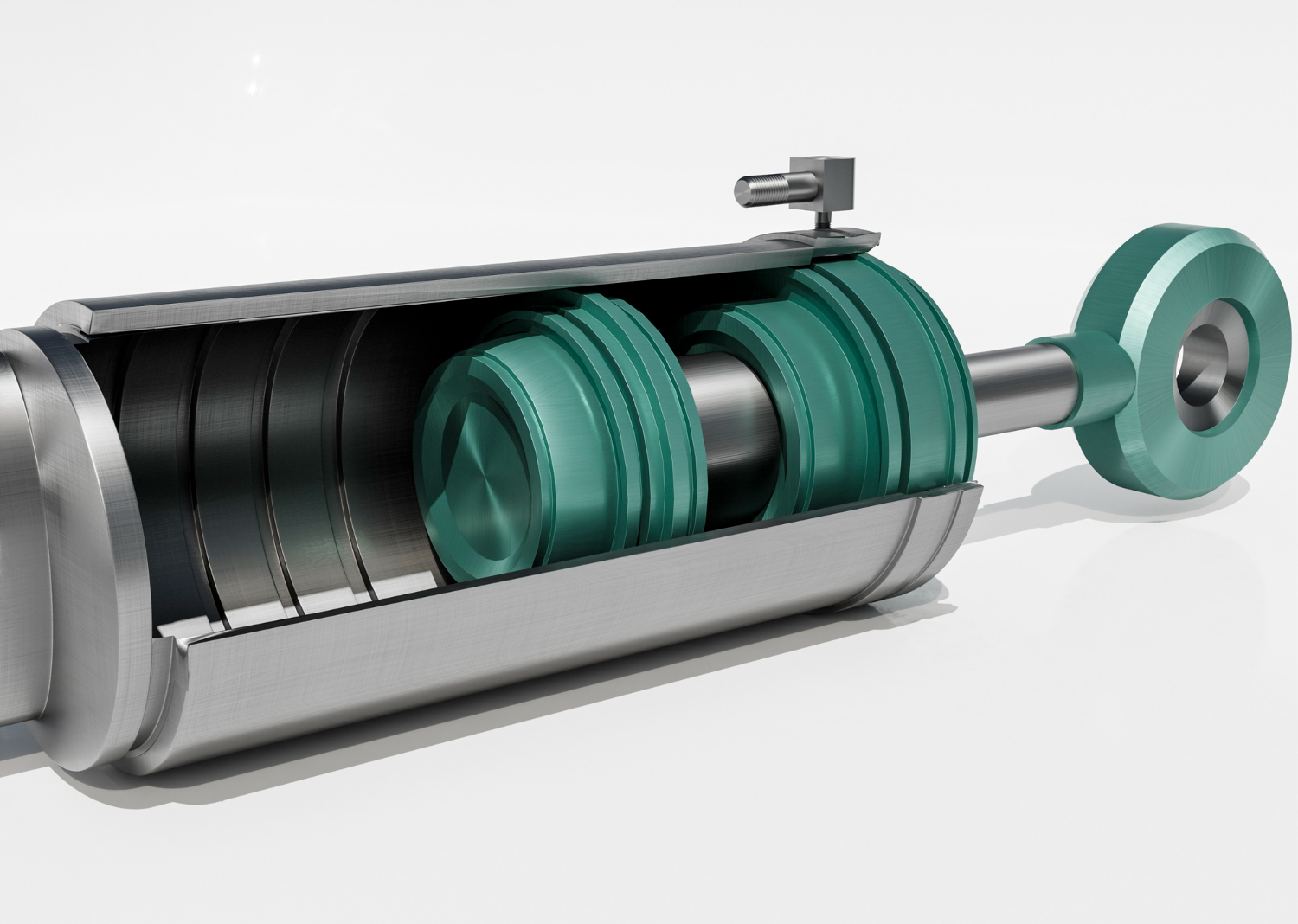
กระบอกสูบไฟฟ้าคือ อะไร มีข้อดี – ข้อเสียอย่างไรกระบอกสูบไฟฟ้าคือ อะไร มีข้อดี – ข้อเสียอย่างไร
กระบอกสูบไฟฟ้า คือ อุปกรณ์ที่มีส่วนช่วยในการเคลื่อนที่แนวตรงโดยได้แรงขับเคลื่อนจากมอเตอร์ไฟฟ้า อีกทั้งยังมีข้อดีหลายประการจึงได้รับความนิยมอย่างมากในงานอุตสาหกรรม แต่อย่างไรก็ตามอย่างมีข้อดีและประโยชน์อื่นที่เรายังไม่พูดถึง ดังนั้นเพื่อเพิ่มความเข้าใจเราจึงจะพาคุณไปทำความรู้จักเกี่ยวกับข้อดี – ข้อเสียและประโยชน์ของกระบอกสูบว่ามีอะไรบ้าง กระบอกสูบไฟฟ้ามีข้อดีอะไรบ้าง เพื่อทำความรู้จักกระบอกสูบไฟฟ้ากันมากขึ้นไปดูกันว่าอุปกรณ์ชนิดนี้มีข้อดีอย่างไร 1. ไม่มีเสียงรบกวน กระบวนการทำงานของกระบอกสูบไฟฟ้า คือ จะเคลื่อนที่เป็นแนวตรงโดยใช้แรงขับเคลื่อนจากมอเตอร์ไฟฟ้าเคลื่อนไปยังบอลสรู จากนั้นจะเคลื่อนที่ไปตามแนวแกนโดยสามารถปรับความเร็วและความแม่นยำได้ตามต้องการ ซึ่งกระบวนการต่าง ๆ เหล่านี้ไม่ก่อให้เกิดเสียงรบกวนใด ๆ ...

ไอเดียของขวัญวันแม่ไอเดียของขวัญวันแม่
เมื่อเข้าสู่เดือนสิงหาคม เราคงจะรู้กันดีกว่าเป็นเดือนแห่งการแสดงความรักกับคุณแม่ เพราะวันที่ 12 สิงหาคมของทุกปีจะเป็นวันแม่แห่งชาติ ซึ่งแน่นอนว่าเรานั้นรักคุณแม่ในทุกๆ วัน แต่ในเดือนนี้เราจะแสดงความรักกับคุณแม่เป็นพิเศษ ด้วยการพาท่านไปทานข้าวนอกบ้าน หรือพาไปเที่ยวพักผ่อน พร้อมมอบของขวัญแสนประทับใจให้กับท่าน วันนี้ใครที่กำลังคิดหนักว่าจะซื้ออะไรเป็นของขวัญวันแม่ดี ก็ไม่ต้องกังวลไปเพราะเรามีไอเดียของขวัญวันแม่ดีๆ มาแนะนำ ไปดูกันเลย นาฬิกาข้อมือ นาฬิกาเป็นเครื่องประดับที่สวมใส่เพื่อความสวยงามและมีประโยชน์ในเรื่องของการดูเวลา ซึ่งเหมาะมากๆ กับทุกเพศทุกวัย เพราะสามารถสวมใส่ได้ในทุกๆ...

ห้องเก็บประจุไฟฟ้าพลังงานแสงอาทิตย์ ทำไมต้องติดตั้งเครื่องควบคุมอุณหภูมิและความชื้นห้องเก็บประจุไฟฟ้าพลังงานแสงอาทิตย์ ทำไมต้องติดตั้งเครื่องควบคุมอุณหภูมิและความชื้น
เครื่องควบคุมอุณหภูมิและความชื้นช่วยควบคุมอุณหภูมิที่เกิดขึ้นภายในห้องและสามารถลด สิ่งแปลกปลอมชนิดต่างๆภายในห้องได้เป็นอย่างดีเช่นฝุ่นละออง ความชื้น และกำจัดกลิ่นไม่พึงประสงค์ภายในห้องได้ ในปัจจุบันอุตสาหกรรมไฟฟ้าพลังงานแสงอาทิตย์ กำลังได้รับความนิยมอย่างแพร่หลายเพราะสามารถให้พลังงานที่บริสุทธิ์ ประหยัดพลังงานหรือไฟฟ้าได้ต่อเนื่อง ไฟฟ้าพลังงานแสงอาทิตย์ถูกผลิตขึ้นจากแผงโซล่าเซลล์เปลี่ยนความร้อนจากแสงแดดให้เป็นพลังงาน ส่งเข้าเก็บประจุไฟฟ้ากับแบตเตอรี่ หากเป็นระบบที่มีขนาดใหญ่จะมีห้องเก็บประจุไฟฟ้าจะมีการติดตั้งเครื่องปรับอากาศหรือเครื่องควบคุมอุณหภูมิและความชื้น เพื่อควบคุมอุณหภูมิระหว่างการชาร์จประจุไฟฟ้าเข้ากับแบตเตอรี่ ทำไมถึงต้องติดตั้งเครื่องควบคุมอุณหภูมิและความชื้น ไว้ภายในห้องเก็บประจุไฟฟ้าพลังงานแสงอาทิตย์ โดยปกติแล้วห้องควบคุมของไฟฟ้าแสงอาทิตย์ที่มีขนาดใหญ่ จะมีการจัดเก็บประจุไฟฟ้าเป็นจำนวนมากโดยใช้แบตเตอรี่หลายตัวการจัดเก็บประจุไฟฟ้าที่เกิดขึ้นส่งผลให้แบตเตอรี่ปล่อยความร้อนสะสมออกมาหากมีแบตเตอรี่จำนวนมากความร้อนก็จะสูงขึ้นมากอย่างรวดเร็ว การติดตั้งเครื่องควบคุมอุณหภูมิและความชื้น ( Precision Air Processor...

สร้างบ้านคุณภาพดีและมีฟังก์ชั่นเหมาะสมด้วยบริษัท Conventureสร้างบ้านคุณภาพดีและมีฟังก์ชั่นเหมาะสมด้วยบริษัท Conventure
บริษัทรับสร้างบ้าน Conventure ถือเป็นอีกหนึ่งบริษัทรับสร้างบ้านที่มีชื่อเสียงและมีผลงานการทำงานที่ขึ้นชื่อในเรื่องคุณภาพและความสวยงาม อีกทั้งยังมีฟังก์ชั่นและแบบบ้านให้เลือกหลากหลายอีกด้วย ทั้งนี้ด้วยความที่ Conventure เป็นบริษัทรับสร้างบ้านที่ค่อนข้างเน้นเรื่องความหรูหราและคุณภาพในการสร้างบ้าน ทำให้หลายคนอาจกลัวว่าราคาในการใช้บริการสร้างบ้านกับ Conventure อาจเป็นอะไรที่ต้องจ่ายสูง แต่ในความเป็นจริงแล้วที่นี่มีงบประมาณที่คำนวณมาแล้วว่าเหมาะสมกับการมีบ้านรูปแบบใดบ้าง โดยในบทความนี้ เราจึงได้รวบรวมแบบบ้านและฟังก์ชั่นของแต่ละแบบของบริษัทรับสร้างบ้าน Conventure ที่มีความนิยมที่สุด โดยให้อยู่ภายใต้งบประมาณ 3 ล้านบาท จะเห็นว่าบ้านทั้ง 4...

รวมไอเดียการทำสีรถยนต์ใหม่ให้ไฉไลกว่าเดิมรวมไอเดียการทำสีรถยนต์ใหม่ให้ไฉไลกว่าเดิม
ก่อนอื่นเราขอพาเพื่อนๆ ไปทำความรู้จักกับประเภทสีของรถยนต์ที่ถูกต้องตามกฎหมายกันก่อน ซึ่งประเภทสีของรถยนต์ที่ถูกต้องตามกฎหมาย มีทั้งหมด 4 ประเภทด้วยกัน ดังนี้ ประเภทสีของรถยนต์ที่ถูกต้องตามกฎหมาย ไอเดียการทำสีรถยนต์ใหม่ให้ไฉไลกว่าเดิม ไอเดียการทำสีรถยนต์ใหม่ให้ไฉไลกว่าเดิมอิงจากเทคนิคง่ายๆ เลย ก็คือ การอิงจากสีรถเดิมเป็นหลัก บวกกับความชอบส่วนตัว เช่น สีรถเดิมเป็นสีบลอน แต่ความชอบคือสีขาวมุก อันนี้ถือว่าไปด้วยกันได้ ได้รถสีใหม่ที่ไฉไลกว่าเดิมแน่นอน ท้ายนี้...
เทคโนโลยีหรือไอทีกำลังมาแรงอย่างมากที่สุดเลยเทคโนโลยีหรือไอทีกำลังมาแรงอย่างมากที่สุดเลย
ในปัจจุบันนี้เทคโนโลยีหรือไอทีนั้นเป็นเรื่องที่เราเองก็ควรที่จะต้องยิ่งให้ความสนใจกันอย่างมากมายเลยเพราะว่าในเรื่องของไอทีนั้นก็เป็นเรื่องที่ดีอย่างมากที่เราก็ควรที่จะต้องให้ความสนใจเพราะยิ่งเราได้ให้ความสำคัญกับเรื่องของเทคโนโลยีแล้วนั้นก็จะส่งผลที่ดีให้กับตัวเราเองได้อย่างที่สุดเลย และแน่นอนว่าในเรื่องของเทคโนโลยีนั้นก็เป็นเรื่องที่เราเองก็จะต้องอย่ามองข้ามไปเลยเนื่องจากว่าเทคโนโลยีนั้นก็จะทำให้เราได้เป็นคนที่มีความรู้ได้มากยิ่งขึ้นเลยและที่สำคัญหากเราได้ให้ความสนใจกันอย่างเต็มที่แล้วกับเรื่องของไอทีก็จะทำให้เราทันสมัยมากขึ้นด้วยเรื่องนี้จึงจัดว่าเป็นเรื่องที่ดีอย่างมาที่เราเองก็ควรที่จะต้องอย่ามองข้ามผ่านเลยเพราะอย่างน้อยในเรื่องของเทคโนโลยีก็จะมีส่วนที่จะช่วยทำให้เรานั้นได้มรความรู้ที่ดีที่ติดตัวเราไปตลอดเลย ทุกสิ่งทุกอย่างในเรื่องของเทคโนโลยีหรือIT เป็นสิ่งที่เราต้องให้ความสนใจและใส่ใจอย่างมาก เรื่องทุกเรื่องนั้นเป็นสิ่งที่ไม่แน่นอนเราจะต้องมีความรู้ในเรื่องของเทคโนโลยีให้มากๆเพราะเราจะได้มีความรู้ที่ติดตัวไปตลอดด้วยและเรื่องนี้ก็จัดว่าเป็นเรื่องที่เราเองจะต้องยิ่งหาความรู้เพิ่มเติมด้วยก็จะเป็นสิ่งที่ดีให้กับตัวเราเองอย่างที่สุด เรื่องของไอทีนั้นก็จึงเป็นเรื่องที่เราจะต้องใส่ใจให้มากที่สุดเพราะอย่างน้อยการที่เราได้ให้ความสนใจและใส่ใจแล้วก็จะส่งผลที่จะช่วยทำให้เรานั้นเป็นคนที่ดียิ่งขึ้นด้วยและแน่นอนว่าเรื่องของไอทีนั้นก็จะช่วยทำให้เราเป็นคนที่มีความรู้ความสามารถที่จะช่วยทำให้เรานั้นยิ่งมีความสุขได้อีกด้วยและหากเราได้รู้จักที่จะให้ความสนใจตรงส่วนนี้แล้วเชื่อว่าจะเป็นเรื่องที่ดีที่จะทำให้เรานั้นยิ่งงมีความสุขกันที่สุดเลย หลากหลายอย่างในเรื่องของเทคโนโลยีนั้นก็เป็นเรื่องที่ดีอย่างมากอย่างน้อยเราก็จะต้องอย่ามองข้ามไปเลยเพราะหากเราไม่มองข้ามไปแล้วก็จะช่วยทำให้เราเป็นคนที่มีความสามารถและมีความรู้ที่เก่งมากขึ้นด้วย ทุกสิ่งทุกอย่างในตอนนี้จึงเป็นเรื่องที่เราเองก็จะต้องอย่าละเลยไปเลยจึงจะดีอย่างมากเพราะอย่างน้อยในเรื่องของเทคโนโลยีหรือไอทีก็จะมีส่วนที่สำคัญอย่างมากที่จะช่วยทำให้เรานั้นเป็นคนที่มีความรู้ความสามารถที่จะต่อยอดให้เราได้เป็นคนที่เก่งยิ่งขึ้นในอนาคตด้วยนั้นเอง...
ไอทีเป็นเทคโนโลยียอดฮิตสำหรับคนในตอนนี้อย่างมากเลยไอทีเป็นเทคโนโลยียอดฮิตสำหรับคนในตอนนี้อย่างมากเลย
ในปัจจุบันนี้ไอทีคือหัวใจหลักที่สำคัญอย่างมากที่สุด ที่เราเองไม่ควรที่จะมองข้ามเพราะว่าในเรื่องของไอทีนั้นก็เป็นเรื่องที่ดีอย่างมากเลยเพราะว่าไอทีก็จะมีของที่มากมายให้เราได้เลือกใช้งานกันทั้งนี้ก็ขึ้นอยู่กับความสะดวกของเราเองด้วยว่าเราสะดวกที่จะใช้เทคโนโลยีหรือไอทีแบบไหนเพราะในตอนนี้ทุกๆอย่างก็เป็นเรื่องที่สำคัญกับเราเองอย่างมากมายเลย เพราะในตอนนี้เราก้จะต้องใช้คอมพิวเตอร์ในการทำงาน ใชโทรศัพท์ในการติดต่อสื่อสารหรือใช้ไอแพตในการพกพาเพื่อการนำเสนองานก็เป้นได้อีกเช่นกันซึ่งหลากหลายอย่างในตอนนี้นั้นก็เป็นเรื่องที่เราจะมองข้ามไปไม่ได้ดังนั้นเราจึงควรที่จะต้องให้ความสำคัญมากๆด้วยจึงจะดีเพราะฉะนั้นในเรื่องของไอทีนั้นก็เป็นสิ่งที่ดีที่เราจะมองข้ามไปไม่ได้เลย เรื่องของไอทีนั้นจึงเข้ามามีบทบาทที่สำคัญอย่างที่สุดและในตอนนี้หากเราได้ให้ความสนใจแล้วนั้นก็จะทำให้เรายิ่งมีความสุขที่สุดและแน่นอนว่าในเรื่องของไอทีนั้นก็จะทำให้เราไม่เกิดเรื่องกังวลใจเลยดังนั้นเรื่องของการทำธุรกิจเกี่ยวกับไอทีนั้นก็เป็นเรื่องที่เราเองก็จะต้องอย่าละเลยหรือมองข้ามไปเลยเพราะฉะนั้นหากเราไม่ละเลยไปแล้วก็จะส่งผลที่ดีที่จะช่วยทำให้เรายิ่งมีความสุขกับเรื่องของไอทีด้วยนั้นเอง การที่เราได้รู้จักที่จะให้ความสนใจกับเรื่องของไอทีนั้นก็จะเป็นเรื่องที่สำคัญอย่างมากเลยและแน่นอนว่าการที่เราได้หาความรู้ในเรื่องของการเล่นไอทีนั้นก็จะช่วยทำให้เรายิ่งมีความสุขที่สุดและที่สำคัญในเรื่องของไอทีก็จะทำให้เราไม่ต้องเกิดความเครียดเลยเพราะเราก็จะยิ่งมีความสนุกอย่างมากด้วย เรื่องของไอทีนั้นจึงเข้ามามีบทบาทที่ดีและสำคัญกับเราเองมากๆด้วยดังนั้นเราจึงควรที่จะต้องอาจจะเปิดอินเตอร์เน็ตเพื่อหาข้อมูลต่างๆได้ก็จะเป็นเรื่องที่ดีอีกเช่นกันและเรื่องของไอทีนั้นเราจึงควรที่จะต้องให้ความสนใจและหาความรู้เป็นประจำด้วยจึงจะทำให้เรายิ่งมีความสุขอย่างมากมายเลย เราจึงควรที่จะต้องใส่ใจกับเรื่องของเทคโนโลยีให้มากที่สุดเพราะการที่เรามีเทคโนโลยีที่ติดตัวแล้วก็จะส่งผลที่ดีให้กับตัวเราเองได้อย่างมากมายด้วยเช่นกัน เรื่องนี้จึงถือว่าเป็นเรื่องที่สำคัญกับเราเองอย่างมากมายที่สุดที่เราจะมองข้ามไปไม่ได้เลยนั้นเอง หากเราได้รู้จักที่จะให้ความสนใจตรงส่วนนี้แล้วก็จะส่งผลที่ดีอย่างมากมายเลยด้วย...

การทำธุรกิจเกี่ยวกับไอทียิ่งเรียนรู้ยิ่งมีกำไรการทำธุรกิจเกี่ยวกับไอทียิ่งเรียนรู้ยิ่งมีกำไร
ในปัจจุบันนี้เรื่องของการทำธุรกิจเกี่ยวกับไอทีนั้นก็เป็นเรื่องหนึ่งที่เราเองก็ควรที่จะต้องให้ความสำคัญให้มากที่สุดเพราะว่าในเรื่องของการทำธุรกิจเกี่ยวกับไอทีนั้นสามารถที่จะได้กำไรกลับมาได้ไม่ยากเลยเพียงแค่เราจะต้องเป็นคนที่ขยันมากๆด้วยเพราะอย่างน้อยในเรื่องของการทำธุรกิจเกี่ยวกับไอทีนั้นหากเรายิ่งเรียนรู้ได้มากเท่าไหร่ก็จะส่งผลที่ดีที่จะช่วยทำให้เรานั้นได้มีกำไรมากขึ้นด้วย และที่สำคัญในการที่เราทำธุรกิจเกี่ยวกับไอทีนั้นเราก็จะต้องมีทุนสำรองในการลงของก่อนด้วยไม่ว่าจะเป็นในส่วนของอุปกรณ์โทรศัพท์หรืออุปกรณ์เกี่ยวกับไอทีนั้นต้องบอกเลยว่าในตอนนี้นั้นเป็นสิ่งที่สำคัญอย่างที่สุดและหากเราได้รู้จักที่จะให้ความสนใจแล้วนั้นก็จะทำให้เรายิ่งเกิดความเพลิดเพลินใจด้วย เพราะในเรื่องของธุรกิจเกี่ยวกับไอทีนั้นก็เป็นเรื่องที่จะต้องลงทุนให้มากๆเพราะอย่างน้อยในการลงทุนสิ่งที่เกี่ยวกับไอทีนั้นก็จะช่วยทำให้เราได้มีกำไรมากขึ้นด้วย เพราะคนจะเปลี่ยนแอคเซสเซอร์รี่โทรศัพท์เป็นประจำอยู่แล้วซึ่งเรื่องนี้จึงจัดว่าเป็นเรื่องที่เราเองก็ควรที่จะต้องอย่าละเลยหรือมองข้ามไปเลยจึงจะส่งผลที่ทำให้เรายิ่งมีความสุขอีกด้วยหากเราเห็นกิจการนั้นเป็นไปด้วยดีก็จะมีกำลังใจที่ดีขึ้นด้วย เราเองจึงควรที่จะต้องรู้จักที่จะต้องเรียนรู้ให้มากๆกับเรื่องของการทำธุรกิจเพราะยิ่งเราทำธุรกิจเกี่ยวกับไอทีได้มากเท่าไหร่ก็จะยิ่งเป็นผลที่ดีกับเราเองด้วยกันทั้งนั้น เพราะการลงทุนนี้จะต้องมีการเปลี่ยนแบบอยู่เสมอดังนั้นมีของใหม่ของเก่าตลอดเราจะต้องเรียนรู้ในเรื่องของการลงทุนและการบริหารให้มากๆเพราะอย่างน้อยก็จะทำให้เรานั้นไม่ขาดทุนและการขายของเกี่ยวกับไอทีของเราก็จะขายได้ง่ายขึ้นด้วย ทุกๆอย่างในเรื่องของการทำธุรกิจเกี่ยวกับไอทีนั้นก็เป็นสิ่งที่สำคัญและเป็นสิ่งที่ดีอย่างมากเลยดังนั้นหากเราได้รู้จักที่จะให้ความสำคัญตรงส่วนนี้แล้วก็จะยิ่งช่วยทำให้เรานั้นได้มีความสุขกับการทำธุรกิจเกี่ยวกับไอทีด้วย ซึ่งเรื่องของไอทีในตอนนี้จึงเข้ามามีบทบาทที่สำคัญอย่างมากมายด้วยที่เราจะต้องอย่าละเลยหรือมองข้ามไปเพราะกำไรก็จะขึ้นอยู่กับการบริหารเงินของตัวเราเองอีกด้วย ดังนั้นเรื่องของไอทีจึงเป็นเรื่องที่สำคัญกับเราเองอย่างมากมายเลยและเป็นเรื่องที่เราจะมองข้ามผ่านไปไม่ได้เลยเพราะทุกบาทที่เราลงทุนไปก็ต้องได้กำไรกลับมานั้นเอง...

